
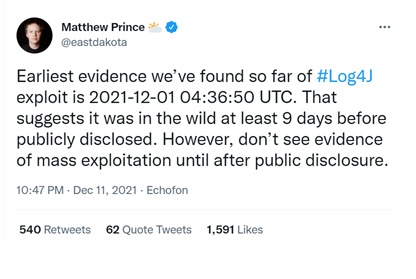
In early December 2021 the Cyber Security world was thrown into disarray with the discovery of Log4Shell, a vulnerability in the Apache Library used in most Java applications which has the potential to let hackers compromise millions of devices on the internet. On Friday, December 9, a severe remote code vulnerability in Apache’s Log4j was announced to the world and tracked as CVE-2021-44228. However, there is some evidence cited by Matthew Prince, CEO of Cloudflare, that it may have been discovered earlier but not disclosed for nine days:
The problem posed by this vulnerability has been described as three-fold:
• It is ubiquitous – found in almost all enterprise software
• It is simple to exploit (12 characters of code is all that is needed to take advantage of it)
• And it is incredibly complex to find and fix.
How does it work?
Log4Shell, is found in Log4j, an open-source logging library used by apps and services across the internet. Logging is a process where applications keep a running list of activities, they have performed, which can later be reviewed in case of error. Nearly every network security system runs some form of logging process, which gives popular libraries like Log4j an enormous reach.
Log4Shell allows remote code execution and access to vulnerable servers, giving malicious hackers the ability to steal data and import malware. To exploit the vulnerability, an attacker has to cause the application to save a special string of characters in the log. Since applications routinely log a wide range of events — such as messages sent and received by users, or the details of system errors — the vulnerability is unusually easy to exploit and can be triggered in a variety of ways.
Cyber researchers at Check Point warned that attackers are scanning the internet for Log4j and that there are over 100 attempts per minute to exploit the weakness. There have been instances of crypto-currency mining malware taking advantage of this as well as several botnets (Miraj, Tsunami and Kinsing) attempting to leverage it.
What is the Scope of the Log4j Vulnerability and how can it affect you?
The size of the problem cannot be underestimated. Jen Easterly, Director of Cybersecurity and Infrastructure Security Agency, described this as the most serious vulnerability she has come across in the decades she has worked in IT:
“This vulnerability, which is being widely exploited by a growing set of threat actors, presents an urgent challenge to network defenders given its broad use. To be clear, this vulnerability poses a severe risk.”
It has been given a severity score of 10 out of 10. As the highest score, this indicates the serious nature of the flaw as it requires little technical knowledge to exploit and can compromise a system without any knowledge or input from the user.
A list of software platforms which have this vulnerability has been compiled and can be reviewed here and it is more than 500 items long but could run to 1000s more:
www.zyxware.com/article/which-software-is-affected-by-log4j-shell-vulnerability
It includes familiar names like Amazon, IBM and Microsoft but also a vast number of companies that enterprise software is built upon like Broadcom, VMware and Red Hat.
How can it affect you?
The diversity of applications vulnerable to the exploit, and range of possible delivery mechanisms, mean that firewall protection alone does not eliminate risk. Theoretically, the exploit could even be carried out physically by hiding the attack string in a QR code that was scanned by a package delivery company, making its way into the system without having been sent directly over the internet.
If in doubt speak to your IT provider to understand if and how you may be impacted.
What can you do to mitigate the problem?
“Test, test, test and patch, patch, patch” states Richard Sharpe amatis Networks.
The first thing is to find out what applications you have that may be vulnerable (see list earlier in this article) or you can test your servers. Then apply the patches and fixes being rolled out by Apache. You can find more details and patches here:
logging.apache.org/log4j/2.x/security.html
Actively monitor for new vulnerabilities – a second weakness was discovered on 14th December 2021; and Apache has released further patches. There is a call to act as quickly as possible to apply the patches, but this is not always possible in larger organisations. First the vulnerabilities have to be found, which can take time, as well as rolling out these protective measures.
Protective action can also be taken at a network level. Cloudflare was one organisation that moved quickly, John Graham-Cumming CTO explains how they added new rules to their firewall products blocking HTTP requests containing strings characteristics of the Log4j attack code. ExpressVPN also modified its product to protect against Log4Shell, updating VPN rules to automatically block all outgoing traffic on ports used by LDAP — a protocol that the exploit uses to fetch resources from remote URLs and download them onto a vulnerable machine.
These actions are not a total fix but they do show that control at a network level can be incredibly useful during a crisis like this. Network level protection has a key role to play since malware programs communicate with their operators over the internet, measures that restrict incoming and outgoing web traffic can provide a stopgap to limit the effects of the exploit.
As we all scrabble to find and patch points of entry perhaps we also need to consider how long this access has been available as Jos Vernon CEO of WebSupergoo commented:
“It’s a ridiculous bug. It must have been exploited for years and years. Presumably if you dare you can look back through your logs and see how long you’ve been hacked for. How many will dare?”
